What iDoperation can do
iDoperation resolves many issues

Manage
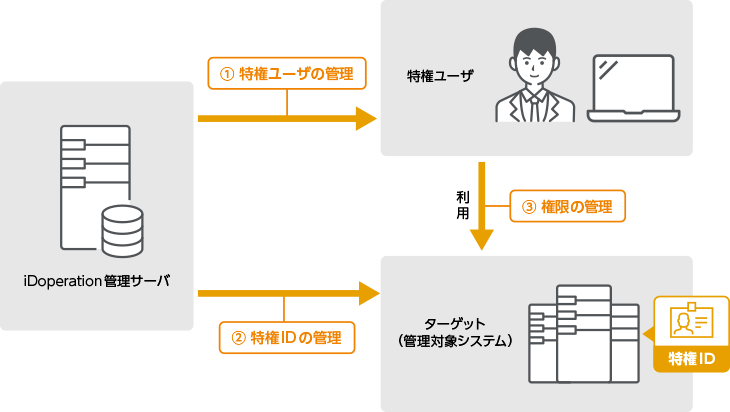
It can visualize privileges, privileged IDs and privileged users
iDoperation captures privileged IDs from a management target system (hereinafter
referred to as the target) and visualizes privileged IDs in the
organization.
The administrator can visualize privileged IDs, privileged users and privileged
access usage rights by registering privileged users and setting permissions.
Functions in progress
Issues resolved ❶
iDoperation becomes a management ledger of identities so you can easily understand privileged IDs, privileged users and privileges.
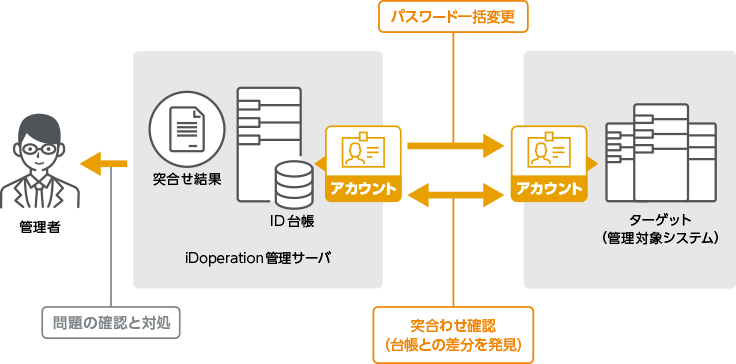
It can automate password changes and account-match inspection
iDoperation automates administrator tasks such as periodic password changes and
account matching.
Administrators can understand management status simply by checking the outcomes
of password changes or account inspection.
Functions in progress
Issues resolved ❷
iDoperation enables automatic batch password changes and account match inspection in accordance with your settings.
Grant
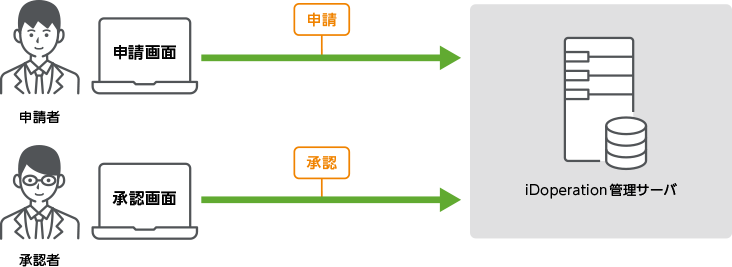
It can provide a privileged access granting and revoking workflow
iDoperation can manage the status of requests and approvals for the granting and
revoking of privileged access. Privileged users apply by indicating the period
of use, purpose of use, work content, and privileged identity as part of the
iDoperation workflow.
The approver verifies and approves or disapproves the request.
Functions in progress
Issues resolved ❸
iDoperation automates privileged access granting and revoking processes by linking them with the workflow.
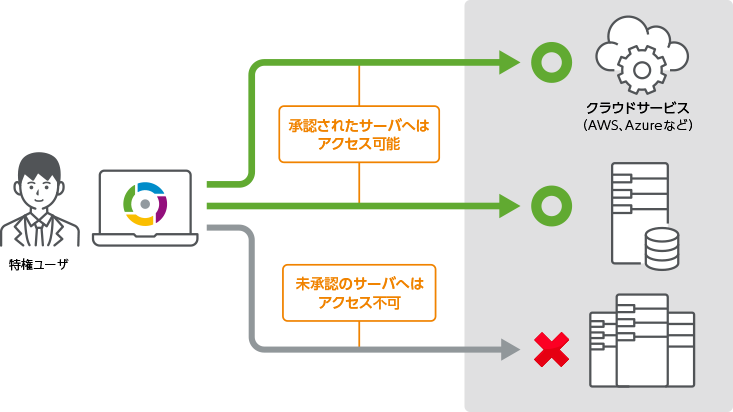
It can grant privileged access temporarily based on approval
iDoperation, upon approval, grants privileged access to a user for an approved
period. Privileged users automatically log in to the server using privileged IDs
granted from iDoperation Client.
Passwords are concealed by iDoperation Client.
Functions in progress
Issues resolved ❹
iDoperation realizes strict access control and use identification by hiding passwords and granting privileged access to authorized users only.
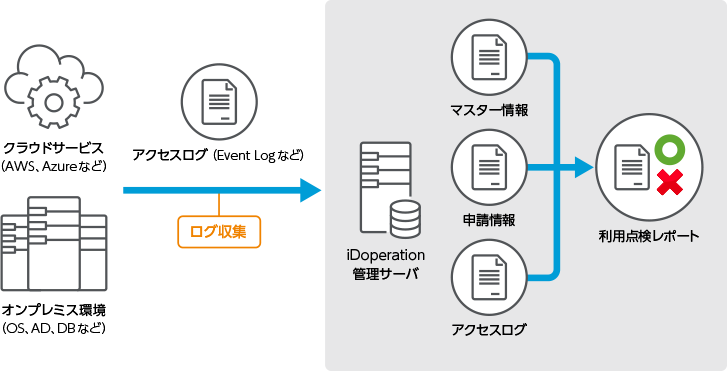
Inspect
It can collect access logs from the target and inspect them
iDoperation collects agentless direct access logs from the target, matches the
collected access logs with the application information, and defines unrequested
access as unauthorized access.
Administrators can detect unauthorized access by simply reviewing the inspection
report.
Functions in progress
Issues resolved ❺ ❻
iDoperation reduces administrator load by collecting access logs and automating inspection for privileged access.
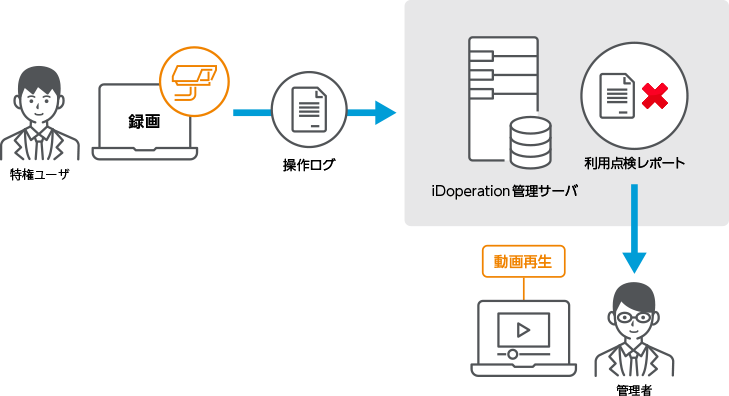
It can record privileged user operation in video
iDoperation records privileged user operation in video.
Administrators can narrow down unauthorized access from privileged access
inspection reports and check actions visually in video.
Functions in progress
Issues resolved ❻
iDoperation lets you narrow down unauthorized access logs and use video to check the details of privileged user operations.