
More about workflow / Privileged access granting
Access granting workflow
Work can proceed even when the approver is absent
If there is a sudden system problem, the approver is absent, etc., you can proceed with operation using post-approval. If a user requires urgent access, an email notification will be sent to the administrator and the user will be required to make a post-operation report. This can achieve a balance between smooth work operation and access control. Urgent access can be permitted or prohibited per workflow.
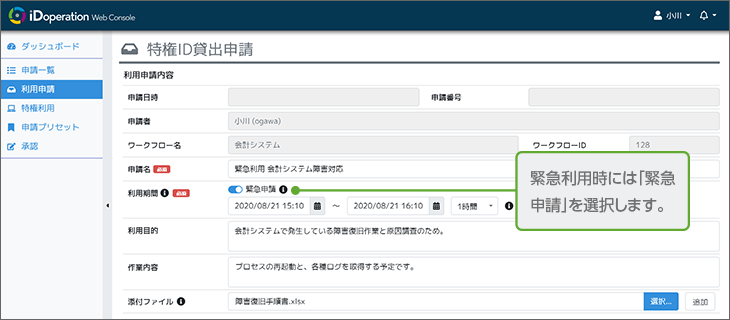
Access granting workflow
Users can customize the application form to suit the work
Users can customize items on privileged access application forms by editing or adding text as desired.
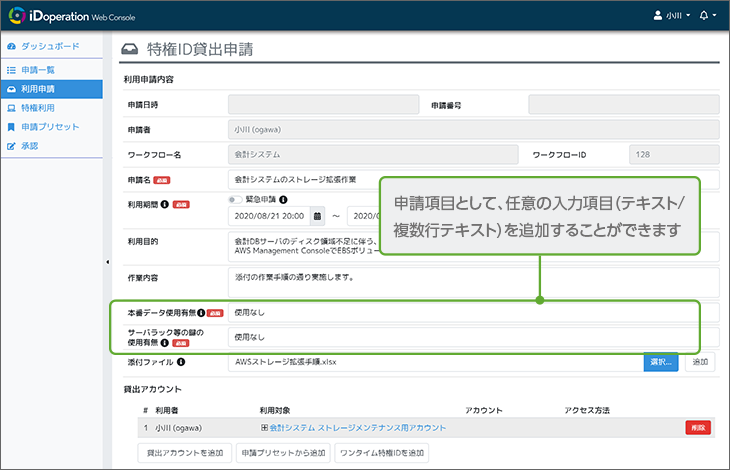
Access granting workflow
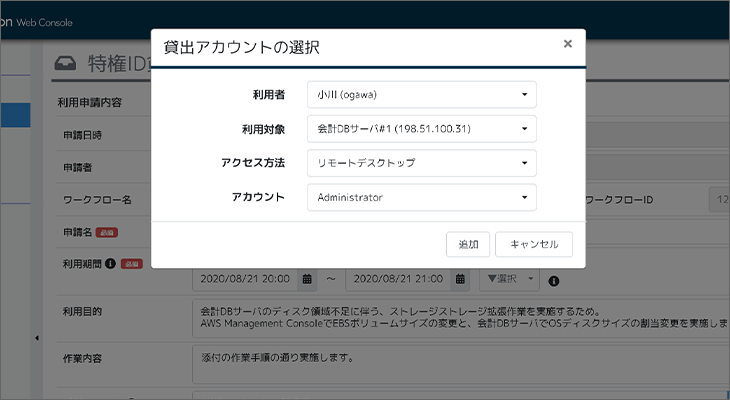
Three ways to choose accounts
When applying for privileged access, users choose a specific privileged ID.
Users specify who uses which privileged identity for which server and application. There are three ways to select accounts: 1) specify a shared privileged ID of the type pre-registered in iDoperation, 2) specify a one-time privileged ID, or 3) specify several privileged IDs together using a preset application form.
Specify a shared privileged ID
Specify one account at a time among registered privileged IDs in iDoperation.
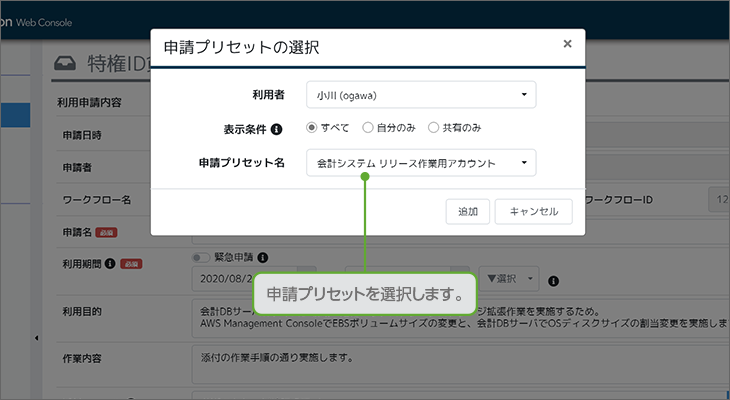
Specify using preset application
By registering multiple targets, accounts and applications in advance, you can specify privileged IDs collectively at the time of the application by simply selecting the preset content.
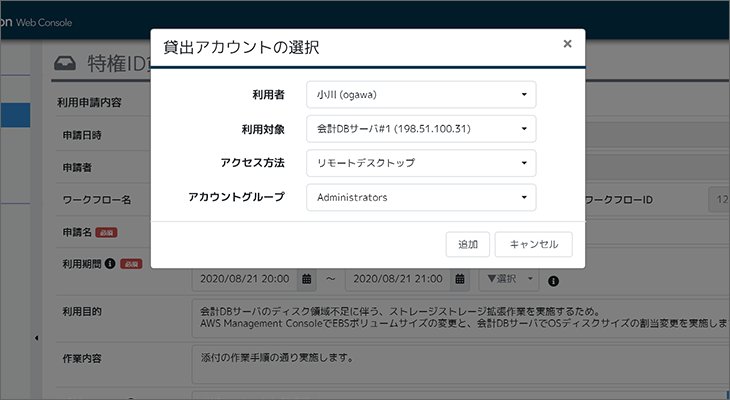
Specify a one-time privileged ID
Specify one one-time privileged ID (only valid during the applied period) at a time. You can choose from multiple account groups depending on what you want to do.
One-time privileged IDs
Cyber attacks are becoming increasingly frequent, and they often target privileged IDs. The challenge is how to prevent attackers from stealing privileged IDs to gain access to PCs and servers and spread malware. By disabling privileged IDs of systems that requires strict security, privileged IDs disappear from the system, so attackers will be unable to steal them.
iDoperation's one-time privileged ID granting allows you to create temporary privileged IDs when necessary on approval, grants them, and automatically deletes or deactivates them after use, strengthening your security.Reporting workflow
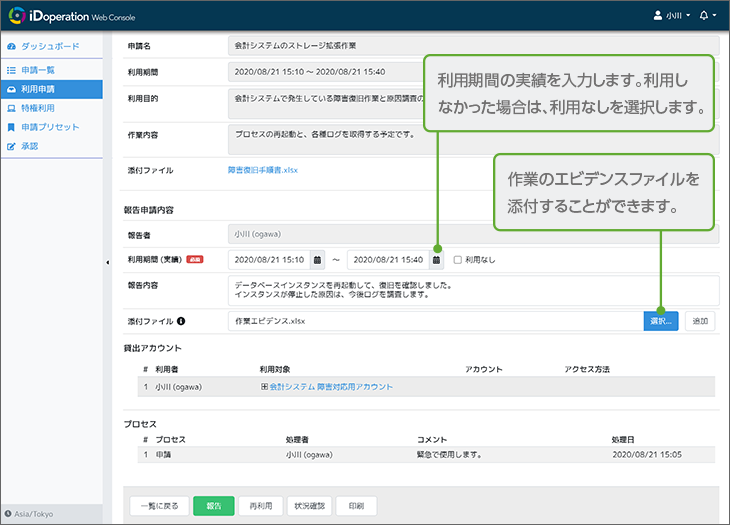
Granted access ends when a report is submitted
Privileged users submit a report via application after finishing the work. The privileged ID is revoked when the report is applied for or the usage period ends. In the case of a one-time privileged ID, the ID is automatically deleted or revoked.
Access granting workflow
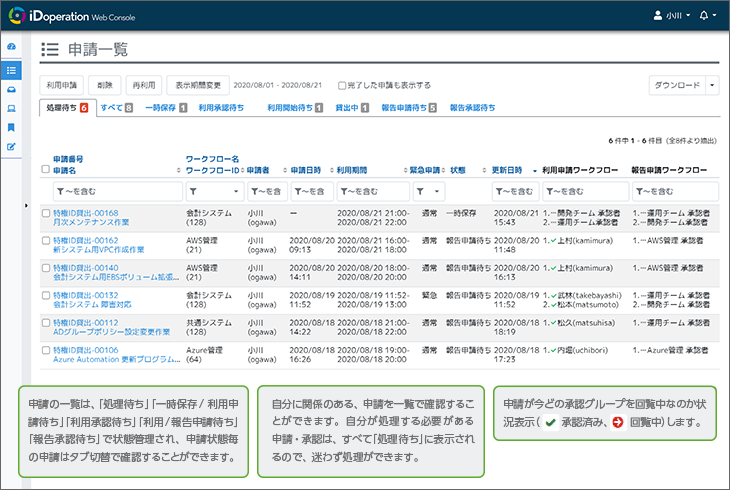
Applications are displayed in an easy-to-understand manner.
All applications are listed and clearly categorized. Those that still require processing by the applicant or approver are under “Waiting” tabs.
Workflow management
It can set workflow suitable for each operation including multi-stage approval
iDoperation can set the workflow separately for each system. Examples of items: approval routes (up to nine levels of approval), permission for emergency applications, maximum granting period for emergency applications, application start date, maximum granting days, granting method (specify an account one by one, specify an account from a preset application form, specify a one-time privileged ID), mandate for report submission.
Granting of privileged access
It can grant privileged access in two ways
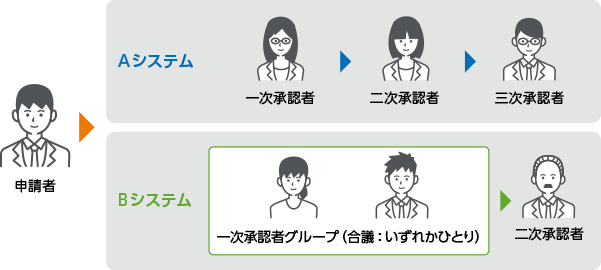
Privileged access can be granted with the password concealed or revealed (one-time password).
For remote access and the like, you can grant privileged access only to authorized privileged users by granting them with the password concealed. If you can't grant passwords confidentially, such as when working on a console, you can grant privileged access only to authorized privileged users by granting them with one-time passwords.
Privileged access granting with the password concealed
iDoperation grants and revokes privileged access to the authorized user, upon approval, at the scheduled day and time.
Access to the target is through single sign-on through iDoperation Client and the password is not revealed to the privileged user. This prevents unauthorized access by unauthorized users.
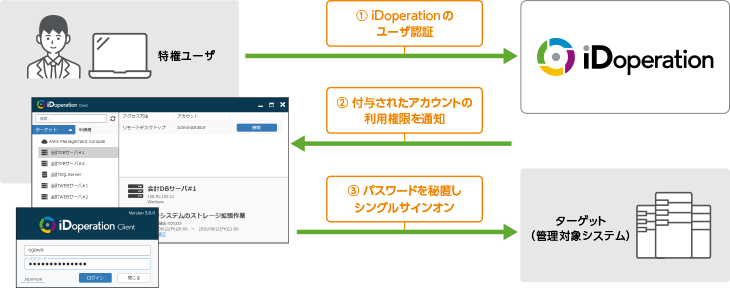
Granting access with one-time password
When local logging in to the target is needed, such as to work with the console, a one-time password can be used. The one-time password is automatically changed to a random password and made invalid when the requested period ends or the usage report is submitted. One-time passwords can be viewed in iDoperation Client or the workflow status window.
Check a password in iDoperation Client
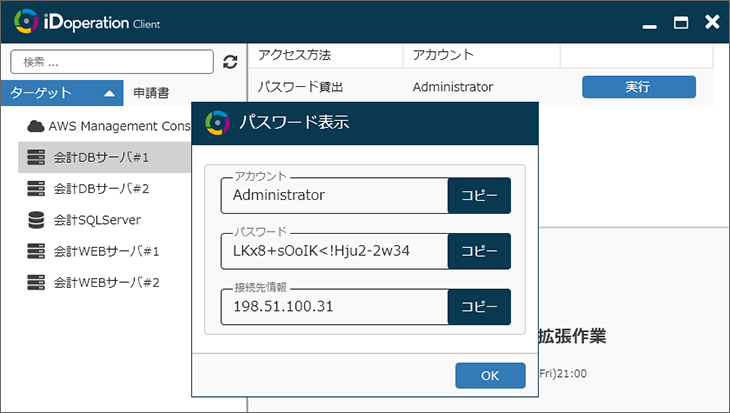
Click "Show password"
Check a password in the workflow status window
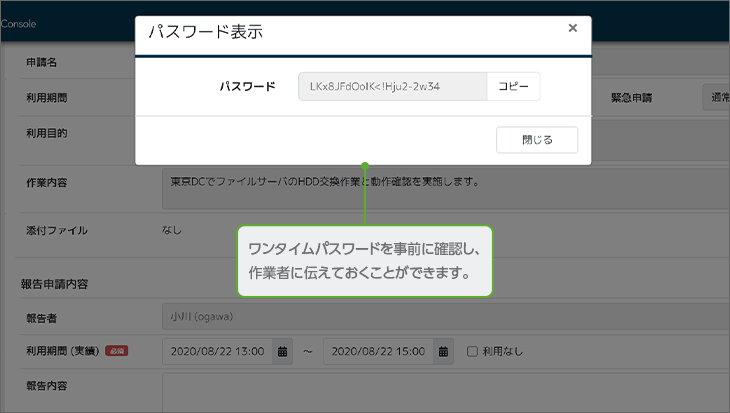
When an application is approved, you can check the one-time password on the status screen.
Granting of privileged access
You can also use Linux key authentication
The use of key authentication, such as Linux on AWS, has been increasing. iDoperation can grant privileged access with a concealed password for Linux that uses key authentication.
As with password-authenticated Linux, privileged users can achieve secure access without being aware of the key.
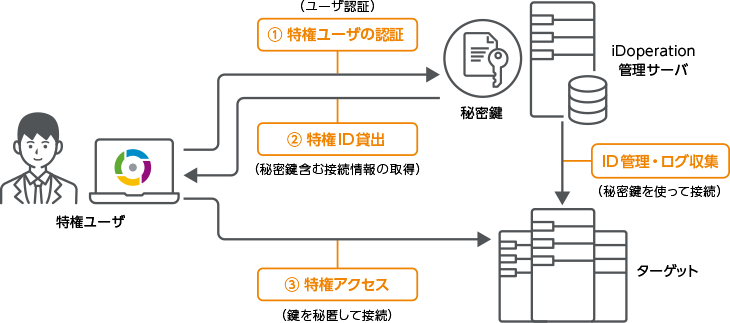
Granting of privileged access
It can increase usability for privileged users by switching the view of iDoperation Client
It helps privileged users handle privileged access with a switchable view.
In addition, iDoperation Client lets you check the application status and information on each target, which helps prevent mistaken access. The iDoperation Client screen supports the English language.
Target View
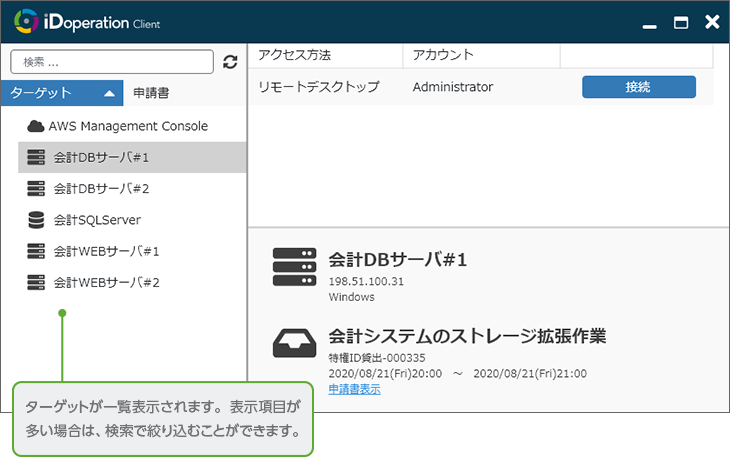
Application view
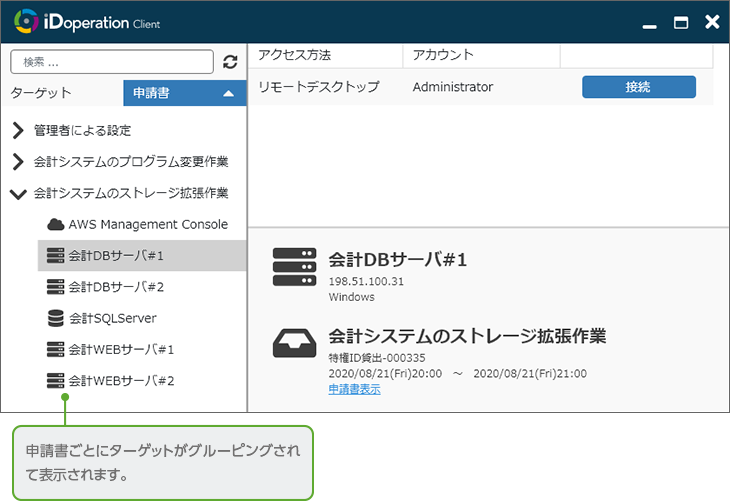
Granting of privileged access
It supports cases when the target belongs to more than one network or the target uses NAT
If the target has more than one IP address, privileged users can still select and access the destination.
For this reason, access control can be performed even in an environment where the network is isolated or in an environment where NAT is performed. In addition, inspection of the access log can be executed reliably.
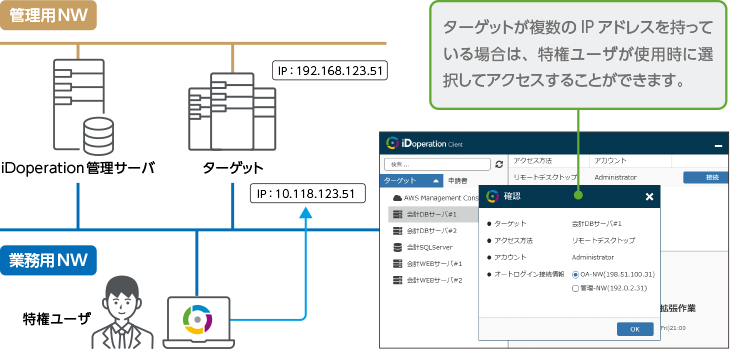
Granting of privileged access
Access granting methods
iDoperation is compatible with applications commonly used in system operation. Applications not standard compatible can be made compatible by your own script extensions.
| Target Type |
Applications that support privileged access granting with the password concealed |
Supports one-time password |
Supports one-time privileged access granting |
|
|---|---|---|---|---|
| OS | Windows | RDP, WinSCP, FFFTP | ○ | ○ |
| Active Directory | RDP | ○ | ○ | |
| Linux, AI, Solari, HP-UX | TeraTerm, WinSCP, FFFTP | ○ | ○ | |
|
Directory Service |
Microsoft Active Directory | RDS | ○ | ○ |
|
AWS Managed Microsoft AD, AWS Simple AD |
- | ○ | ○ | |
|
Virtualization Software |
vSphere ESXi | vSphere Client, VMware Host Client | ○ | × |
| vCenter Server Appliance | vSphere Web Client(*1) | ○ | × | |
| Hyper-V Server | RDP | ○ | × | |
| Database | Oracle, Amazon RDS for Oracle | SQL*Plus | ○ | × |
|
SQL Server,Azure SQL Database,
Amazon RDS for SQL Server |
SQL Server Management Studio | ○ | × | |
| PostgreSQL | - | ○ | × | |
| MariaD, Amazon RDS for MariaDB | - | ○ | × | |
| MySQL | MySQL Command Line Client | ○ | × | |
| Db2 | Db2 CLPPlus | ○ | × | |
| HiRDB | HiRDB SQL Executer(line mode version) | ○ | × | |
| Cloud | AWS Management Console(IAM) | AWS Management Console(*1) | ○ | ○ |
| Azure AD | Azure Portal(*1, Office 365(*1) | ○ | × | |
| BOX | BOX | × | × | |
|
Googole Cloud Platform(*1), Google Workspace(*1) |
○ | × | ||
| Oracle Cloud Infrastructure(IAM) | Oracle Cloud Infrastructure Console(*1) | × | × | |
| Salesforce | Salesforce(*1) | ○ | × | |
| Application | iDoperation(administrator) | iDoperation Web Console(*1) | ○ | × |
- (*1)
- Supported browsers are Microsoft Edge, Google Chrome, and Safari.
