Other
iDoperation external collaboration function
Products that iDoperation can collaborate with (standard)
iDoperation can work in collaboration with the following products as a standard feature.
| Classification | Product | Description |
|---|---|---|
| Granting of privileged
access (workflow collaboration) |
Working with ServiceNow workflows, you can complete privileged access applications and approvals on ServiceNow. iDoperation Connector is required. | |
| Inspection for
privileged access (access log collaboration) |
ALog EVA | Integrated management of iDoperation logs at ALog EVA enables trend analysis of privileged user behavior, early detection of signs of unauthorized access, long-term log storage, integrated log management, and cross-search. |
| Integrated management of iDoperation logs at Logstorage provides cross-sectional analytics integrated with logs from other systems, long-term storage of logs, and flexible reporting. Logstorage iDoperation collaboration package is required. | ||
| Inspection for
privileged access (operation log collaboration) |
ALog ConVerter | Once ALog ConVerter logs are imported into iDoperation SC, you can play cued onscreen operation videos from the imported logs. |
| CWAT | Once CWAT logs are imported into iDoperation SC, you can play cued onscreen operation videos from the imported logs. | |
| LANSCOPE on-premises version | Once LANSCOPE on-premises version logs are imported into iDoperation SC, you can play cued onscreen operation videos from the imported logs. | |
| MaLion6 | Once MaLion6 logs are imported into iDoperation SC, you can play cued onscreen operation videos from the imported logs. | |
| MylogStar | Once MylogStar logs are imported into iDoperation SC, you can play cued onscreen operation videos from the imported logs. | |
| SS1 | Once SS1 logs are imported into iDoperation SC, you can play cued onscreen operation videos from the imported logs. |
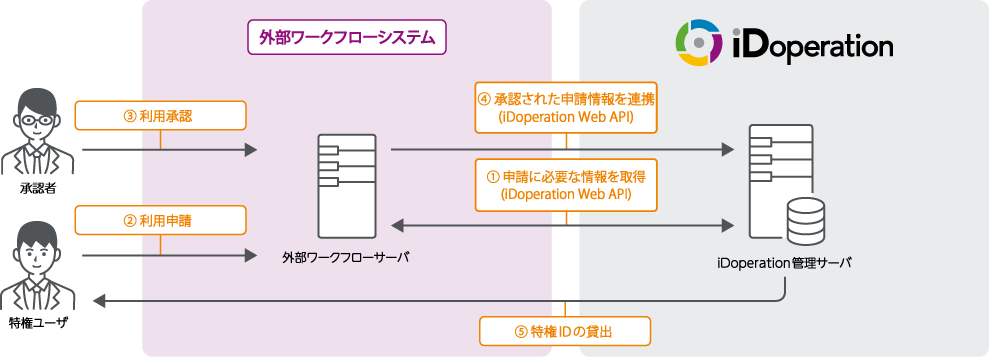
Granting of privileged access using the external collaboration function
External workflow collaboration function
Privileged access can be granted without using the iDoperation workflow by using
collaborating application information approved in an external workflow system.
Users can use the existing workflow system to apply for privileged access. Two methods of collaborating with external workflow systems are provided: CSV collaboration and iDoperation Web API collaboration.
● Collabpration with CSV
Application information on the privileged access approved by the external workflow system is output into a CSV format file and captured into iDoperation. The privileged access will be granted based on the captured application information.
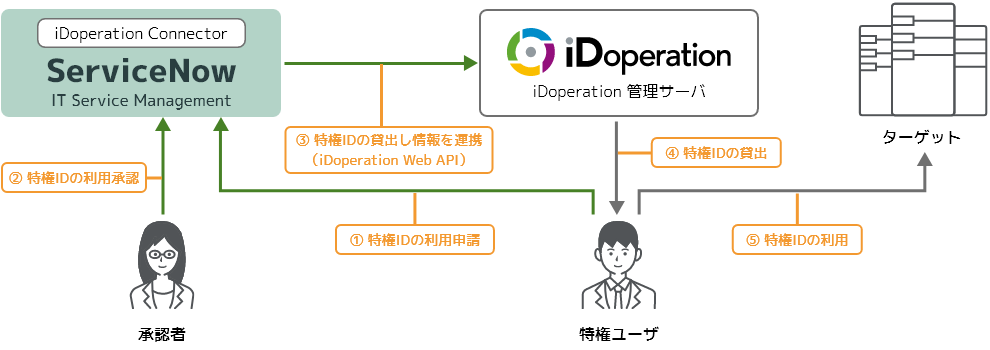
● Collaboration with the iDoperation Web API (Collaboration with ServiceNow using the iDoperation Connector)
You can work with iDoperation and ServiceNow by using iDoperation Connector. When a privileged access is applied and approved through ServiceNow IT Service Management digital workflows, iDoperation shares the result and automatically grants a privileged access. iDoperation Connector is a ServiceNow Flow Designer template that includes 13 flows and actions related to granting privileged access, registering privileged users, and so on, and is available from the Service Now Store's Japanese website.
● Collaboration with iDoperation Web API
Privilege access is granted and revoked by using the iDoperation Web API to interact with application information and report information approved by an external workflow system.
Note: As an iDoperation Web API for collaborating with external systems, APIs are provided for "Obtaining a list of user information," "Obtaining a list of targets and account information", "Obtaining a list of access methods", "Obtaining a list of application information", and "Granting and revoking of privileged access".
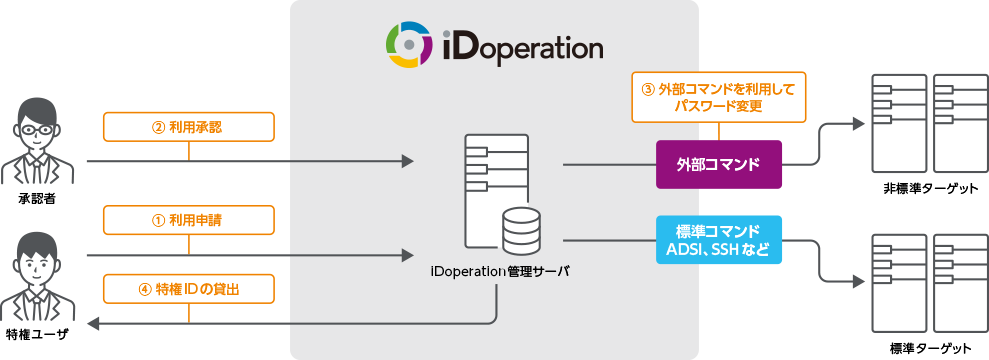
External identity management collaboration function
By using external commands (that you develop separately) for targets that iDoperation
does not natively support, you can manage accounts in synchronous mode as with standard targets.
This enables iDoperation to automate the management of all systems that have an IP address and authenticate using IDs and passwords.
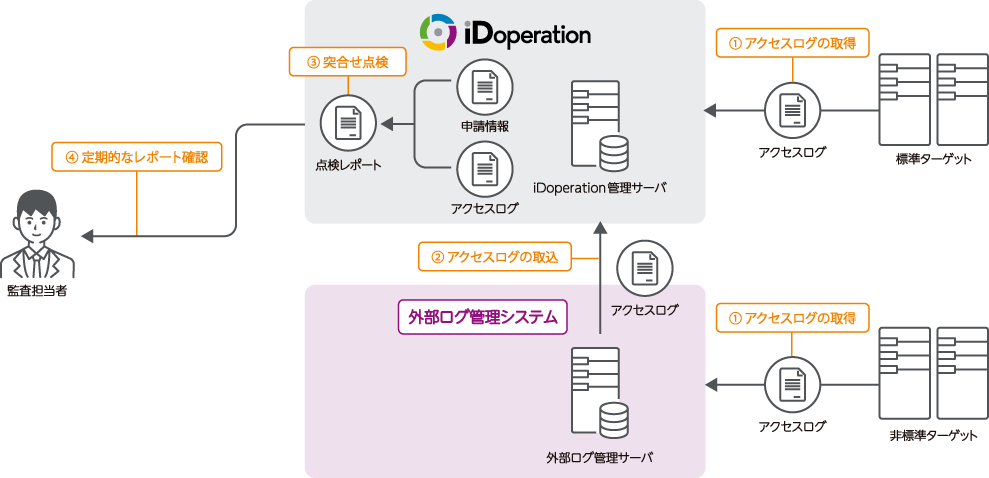
Inspection of privileged access using the external collaboration function
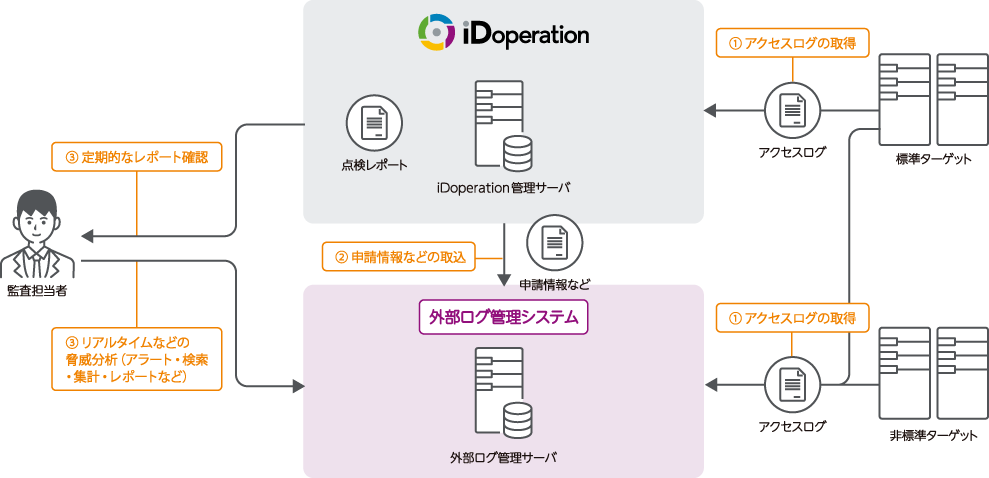
External access log collaboration function
You can inspect use of privileged access in collaboration with an external log management system. There are two methods: inspecting in iDoperation and inspecting in the external log management system.
● Inspection in iDoperation
Target systems that do not provide standard support for iDoperation (targets that cannot automatically collect access logs) can be inspected for privileged access just like standard targets by importing access logs from an external log management system.

● Inspection with external log management
It can centralize management of logs by linking iDoperation application, log, and report information with an external log management system (such as SIEM/log management products). By using the various information from iDoperation in external log management systems, you can increase the likelihood of detecting unusual activity.
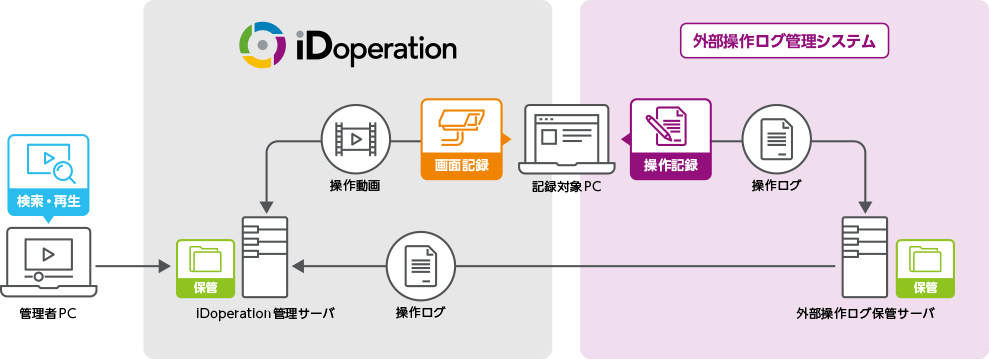
External operation log collaboration function
You can import text operation logs recorded on external log recording products into iDoperation and search them in the iDoperation search screen. Corresponding onscreen operation videos are automatically cued in operation log searches for playback.
● Image of collaboration with other log products