Privileged access inspection
Privileged access inspection
iDoperation acquires comprehensive access logs and inspects them automatically against the application information. Efficient inspection can be performed by automatically discovering unauthorized access (access not applied for) and checking the operation video of such access.
Access log inspection
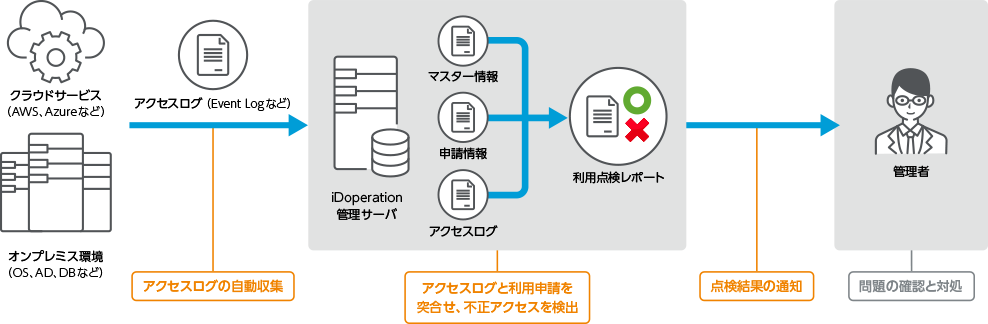
It collects access logs from privileged users and automatically inspects them.
iDoperation collects direct access logs from the target without an agent,
matches them against the application information, and defines unapplied access
as unauthorized.
Administrators can detect unauthorized access by simply
reviewing inspection reports. There is no inspection leakage because access logs
are collected regardless of the route, such as for remote access, local access
and multi-stage access from and to the server, where log collection leaks are
most likely to occur.
Access log collection
iDoperation automatically collects access logs from managed targets. Because it collects logs directly from targets without the use of an agent, it can collect logs for local and remote access.
Access log inspection
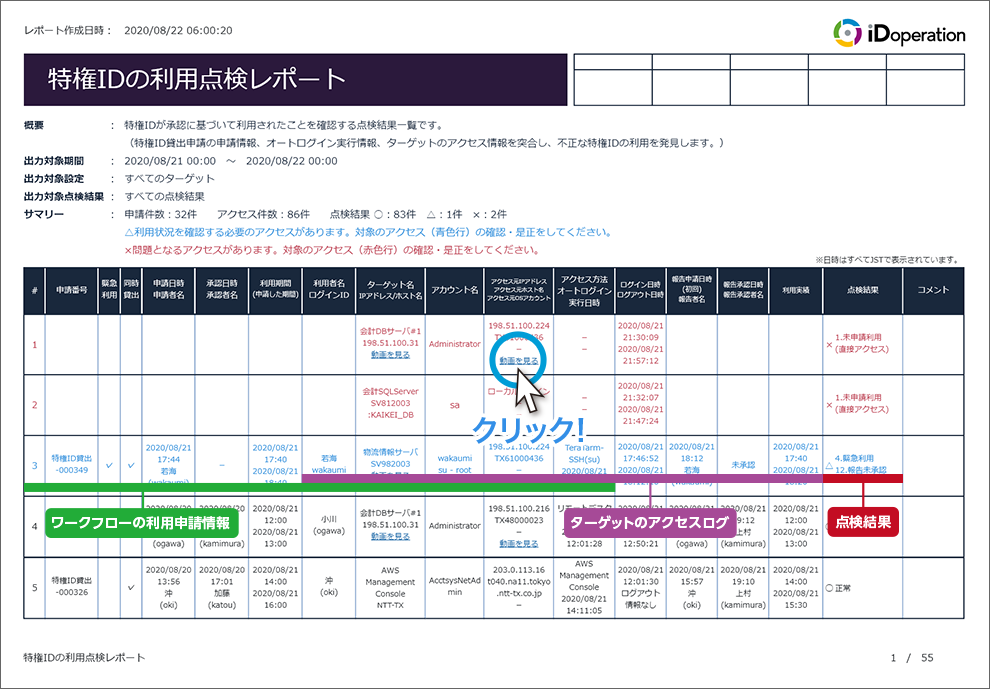
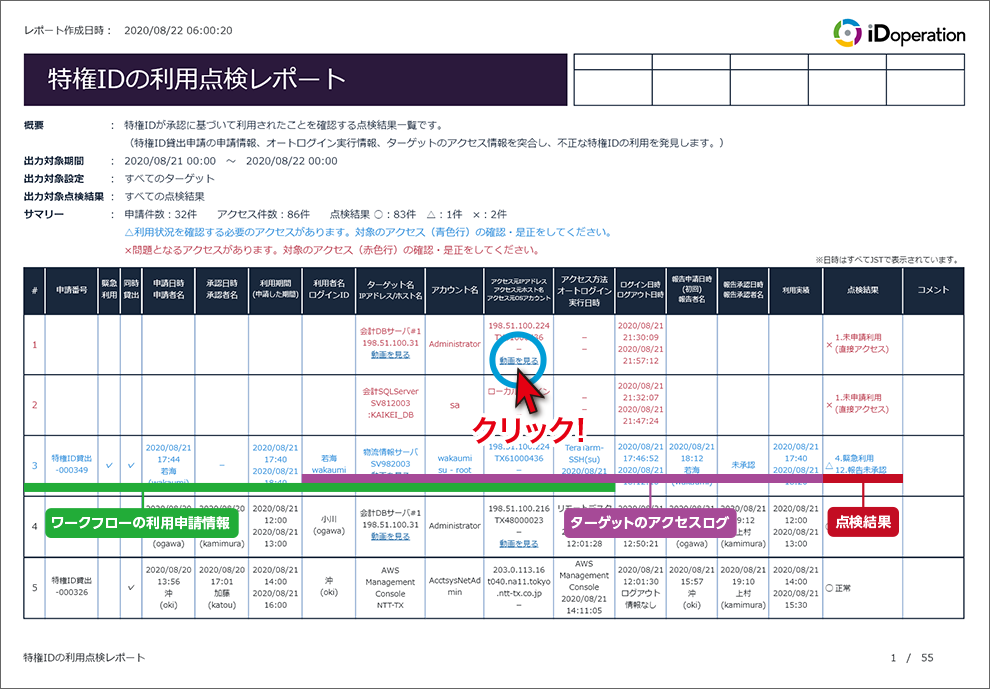
iDoperation collects access logs from the target, then matches them against application information, and access that don't correspond to an application are defined as unauthorized. You can view the results of the access log inspections in an easy-to-understand inspection report.
Inspection report
iDoperation outputs the results of the access log inspections in an easy-to-understand inspection report. You can check if there are any issues by simply viewing the summary.
Email notifications
If there is an alert (△) or an issue (×) in the result, you can send an email notification to the administrator.
Operation log inspection
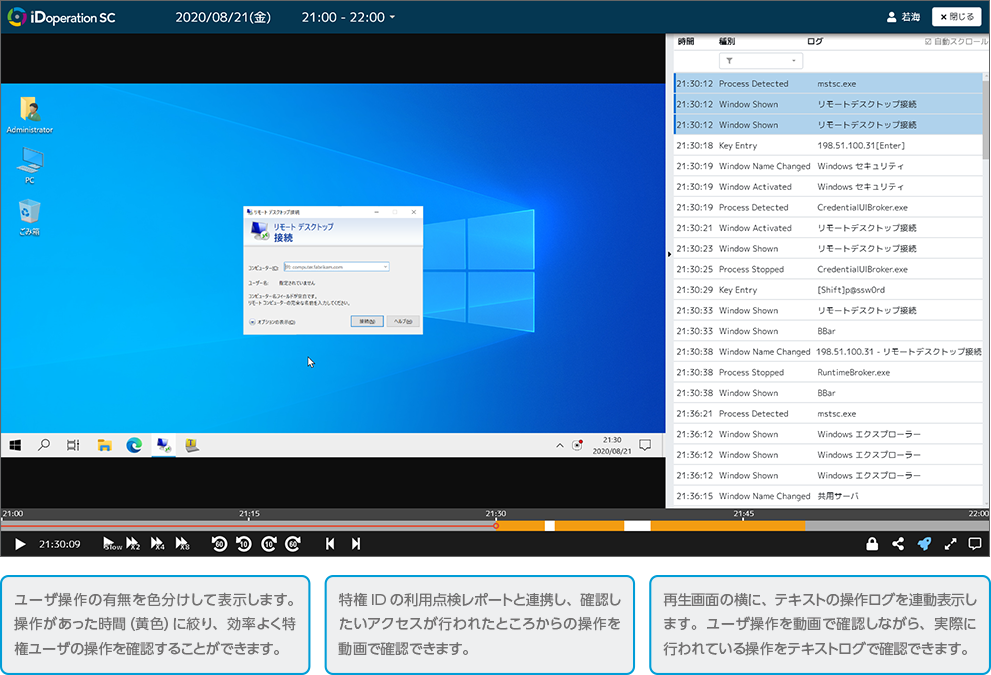
It can video-record the operation of previleged users
iDoperation records the onscreen operations of privileged
users.
Administrators can narrow down unauthorized access (access not yet
applied for), from inspection reports and visually inspect the operation.
Screen operation recording
iDoperation records the onscreen operations of privileged users. By working in conjunction with the inspection report, you can view the onscreen operations of unauthorized access.
Operation log recording
iDoperation also retrieves text-format operation logs (key input, process startup, window titles, and USB device insertion and removal). You can search the operation logs and cue videos.
How to inspect privileged access
Ideally, all operations performed by privileged users should be inspected. However, if there are many users and it is unrealistic to inspect all of them, you can inspect them in samples. Since iDoperation checks all access logs, you can narrow them down to with problematic access for efficient sampling inspections.Report
It can visualize access conditions and unauthorized access
The access log manage function of iDoperation can provide the three types of reports below, in English, in the PDF or Excel format.
| Classification | Report | Content and usage |
|---|---|---|
|
Privileged access log inspections |
A list of inspection results that clarify if privileged access was approved. It detects unauthorized access by matching the actual access log with application information. | |
| List of all logins and logouts for targets | ||
|
List of failed logins to targets. This history reveals unauthorized access. |
Initiative for responding to constantly changing environments and audits
The iDoperation inspection report was developed with prior review by auditing firms. When changes in the environment or laws and guidelines require attention, product updates take priority.
- *
- A separate contract for support services is required.